Winutils Exe Hadoop Download For Mac

README.md winutils Windows binaries for Hadoop versions These are built directly from the same git commit used to create the official ASF releases; they are checked out and built on a windows VM which is dedicated purely to testing Hadoop/YARN apps on Windows. It is not a day-to-day used system so is isolated from driveby/email security attacks. Security: can you trust this release? • I am the Hadoop committer ' stevel': I have nothing to gain by creating malicious versions of these binaries.
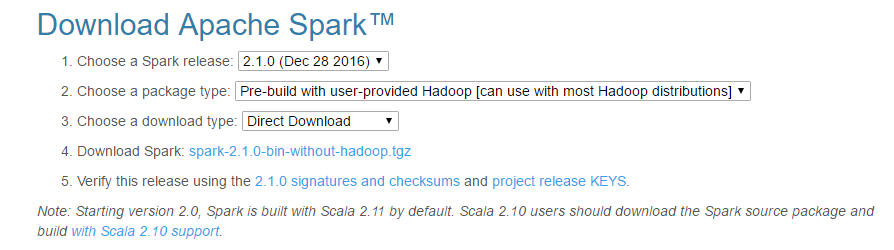
Winutils free download - WinUtilities Free Edition, WinUtilities Professional Edition, WinUtilities Free Undelete, and many more programs. Feb 16, 2017 - Installing Spark in Standalone Mode. In this section I will cover deploying Spark in Standalone mode on a single machine using various platforms. Feel free to choose the platform that is most relevant to you to install Spark on. Getting Spark. In the installation steps for Linux and Mac OS X, I will use pre-built.
If I wanted to run anything on your systems, I'd be able to add the code into Hadoop itself. • I'm signing the releases. • My keys are published on the ASF committer keylist.
• The latest GPG key (E7E4 26DF 6228 1B63 D679 6A81 950C C3E0 32B7 9CA2) actually lives on a yubikey for physical security; the signing takes place there. 3dm Gta V Crack V7. • The same pubikey key is used for 2FA to github, for uploading artifacts and making the release. Someone malicious would need physical access to my office to sign artifacts under my name. If they could do that, they could commit malicious code into Hadoop itself, even signing those commits with the same GPG key. Though they'd need the pin number to unlock the key, which I have to type in whenever the laptop wakes up and I want to sign something. That'd take getting something malicious onto my machine, or sniffing the bluetooth packets from the keyboard to laptop.
Were someone to get physical access to my machine, they could probably install a malicous version of git, one which modified code before the checkin. I don't actually my patches to verify that there's been no tampering, but we do tend to keep an eye on what our peers put in. The other tactic would have been for a malicious yubikey to end up being delivered by Amazon to my house. I don't have any defences against anyone going to that level of effort. 2017-12 Update That key has been revoked, though it was never actually compromised. Lack of randomness in the prime number generator on the yubikey, hence. Not set things up properly again.
Note: Artifacts prior to Hadoop 2.8.0-RC3 [were signed with a different key](; again, on the ASF key list. Build Process A dedicated Windows Server 2012 VM is used for building and testing Hadoop stack artifacts. It is not used for anything else. This uses a VS build setup from 2010; compiler and linker version: 9.01 for x64 >CL Microsoft (R) C/C++ Optimizing Compiler Version 9.01 for x64 Copyright (C) Microsoft Corporation.
All rights reserved.```` >LINK /VERSION Microsoft (R) Incremental Linker Version 9.01 Copyright (C) Microsoft Corporation. All rights reserved. Maven Fa 18 Hornet Fsx Sdk here. 3.3.9 was used; signature checked to be that of. While my key list doesn't directly trust that signature, I do trust that of other signatorees: C: Work hadoop-trunk>mvn --version Apache Maven 3.3.9 (bb52d8502b132ec0a5a3f4c8323dc5; 2015-11-10T16:41:47+00:00) Maven home: C: apps maven bin.
README.md winutils Windows binaries for Hadoop versions These are built directly from the same git commit used to create the official ASF releases; they are checked out and built on a windows VM which is dedicated purely to testing Hadoop/YARN apps on Windows. It is not a day-to-day used system so is isolated from driveby/email security attacks. Security: can you trust this release? • I am the Hadoop committer ' stevel': I have nothing to gain by creating malicious versions of these binaries. If I wanted to run anything on your systems, I'd be able to add the code into Hadoop itself. • I'm signing the releases. • My keys are published on the ASF committer keylist.
• The latest GPG key (E7E4 26DF 6228 1B63 D679 6A81 950C C3E0 32B7 9CA2) actually lives on a yubikey for physical security; the signing takes place there. • The same pubikey key is used for 2FA to github, for uploading artifacts and making the release. Someone malicious would need physical access to my office to sign artifacts under my name. If they could do that, they could commit malicious code into Hadoop itself, even signing those commits with the same GPG key. Though they'd need the pin number to unlock the key, which I have to type in whenever the laptop wakes up and I want to sign something.
That'd take getting something malicious onto my machine, or sniffing the bluetooth packets from the keyboard to laptop. Were someone to get physical access to my machine, they could probably install a malicous version of git, one which modified code before the checkin. I don't actually my patches to verify that there's been no tampering, but we do tend to keep an eye on what our peers put in. The other tactic would have been for a malicious yubikey to end up being delivered by Amazon to my house. I don't have any defences against anyone going to that level of effort.
2017-12 Update That key has been revoked, though it was never actually compromised. Lack of randomness in the prime number generator on the yubikey, hence. Not set things up properly again. Note: Artifacts prior to Hadoop 2.8.0-RC3 [were signed with a different key](; again, on the ASF key list. Build Process A dedicated Windows Server 2012 VM is used for building and testing Hadoop stack artifacts. It is not used for anything else. This uses a VS build setup from 2010; compiler and linker version: 9.01 for x64 >CL Microsoft (R) C/C++ Optimizing Compiler Version 9.01 for x64 Copyright (C) Microsoft Corporation.
All rights reserved.```` >LINK /VERSION Microsoft (R) Incremental Linker Version 9.01 Copyright (C) Microsoft Corporation. All rights reserved. Maven 3.3.9 was used; signature checked to be that of. While my key list doesn't directly trust that signature, I do trust that of other signatorees: C: Work hadoop-trunk>mvn --version Apache Maven 3.3.9 (bb52d8502b132ec0a5a3f4c8323dc5; 2015-11-10T16:41:47+00:00) Maven home: C: apps maven bin.